Have you ever received an email that seemed too good to be true? Maybe it promised a big prize or claimed your account was in danger.
These messages might be phishing attempts, one of the most common cyber threats today. Phishing attacks trick millions of people every year.
They can steal your personal information, drain your bank account, or take control of your online accounts. The scary part? These scams are becoming increasingly difficult to spot.
In this blog, I’ll show you exactly what phishing is, how these attacks work, and give you 10 practical ways to protect yourself.
By the end, you’ll know how to spot fake messages and keep your information secure.
What Is Phishing?
Phishing is a type of cyberattack in which criminals impersonate trusted companies or individuals. They send fake emails, texts, or create fake websites to steal your personal information.
The word “phishing” sounds like “fishing”, and that’s no accident. Just like fishing, scammers cast a wide net, hoping someone will take the bait.
What do phishers want? They target your passwords, credit card numbers, Social Security numbers, bank account details, and personal information that they can sell.
Common phishing targets include: Email accounts, online banking, social media profiles, shopping websites, and work systems.
How Phishing Attacks Work?
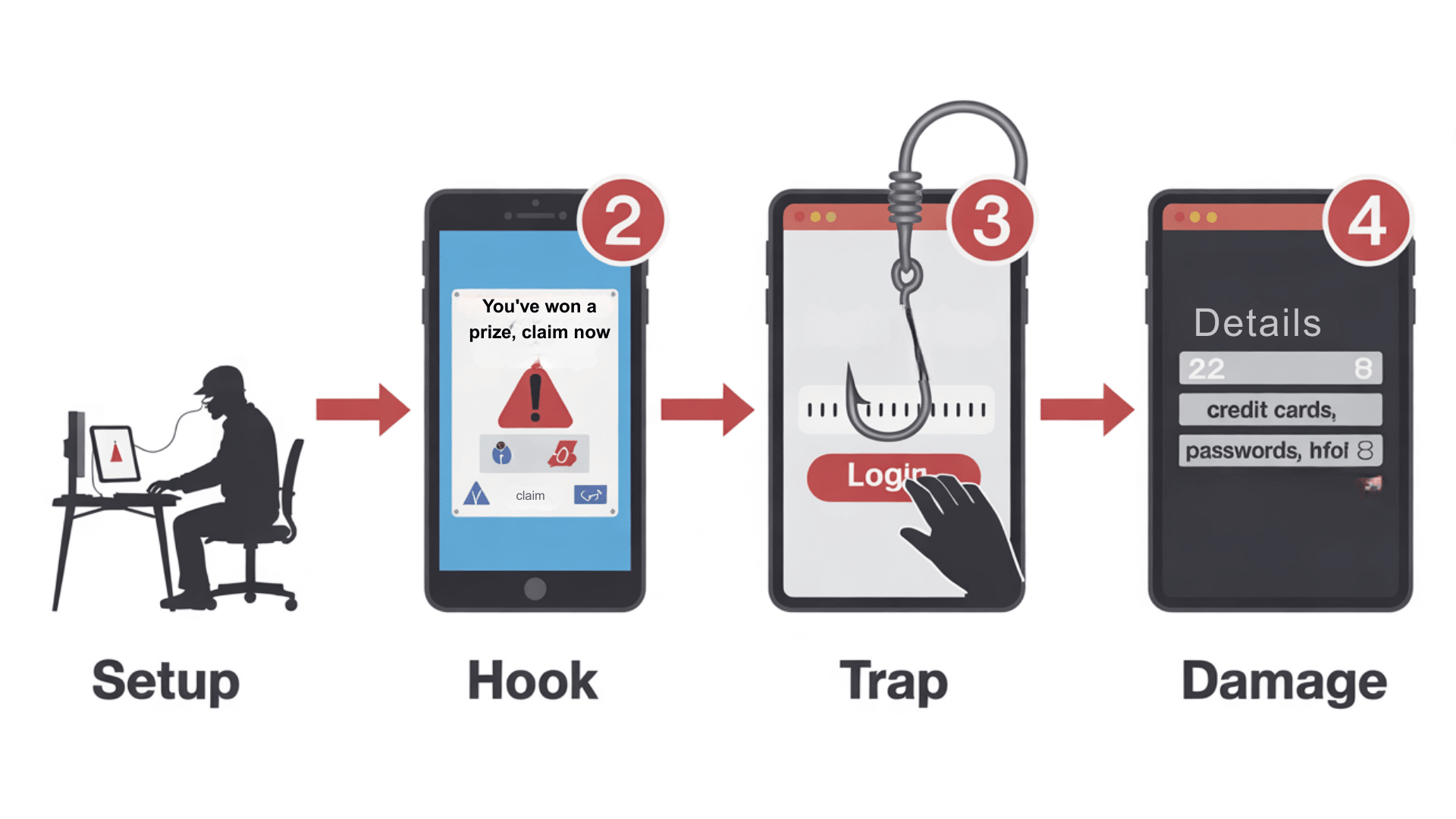
Understanding how phishing works helps you spot the warning signs. Here’s the typical process:
Step 1: The Setup
Criminals research their targets and create convincing fake messages. They copy logos, writing styles, and layouts from real companies. This preparation makes their scams look legitimate and trustworthy.
Step 2: The Hook
You receive a message that creates a sense of urgency or fear. The goal is to make you act without thinking.
- “Your account will be closed in 24 hours.”
- “Suspicious activity detected.”
- “You’ve won a prize, claim now.”
- “Update your payment information.”
Step 3: The Trap
The message includes a link or attachment. Clicking takes you to a fake website that appears to be real. When you enter your information, it is captured instantly by criminals.
Step 4: The Damage
With your stolen information, criminals can access your accounts, make purchases with your credit cards, apply for loans in your name, or sell your data to other criminals.
Common Types of Phishing Attacks
Different types of phishing employ various methods to deceive you.
| Type | Method | Warning Signs |
|---|---|---|
| Email Phishing | Fake emails from banks, retailers, or services | Generic greetings, urgent language, suspicious sender addresses, and poor grammar |
| Spear Phishing | Targeted attacks using your personal information | Highly personalized content appears from known contacts, hard to detect |
| Smishing (SMS) | Phishing through text messages | Unknown numbers, urgent messages, suspicious links, requests to call back |
| Vishing (Voice) | Phone calls from fake representatives | Unsolicited calls, pressure tactics, and requests for personal info over the phone |
| Pharming | Redirecting to fake websites automatically | Website looks wrong, URL doesn’t match, missing security features |
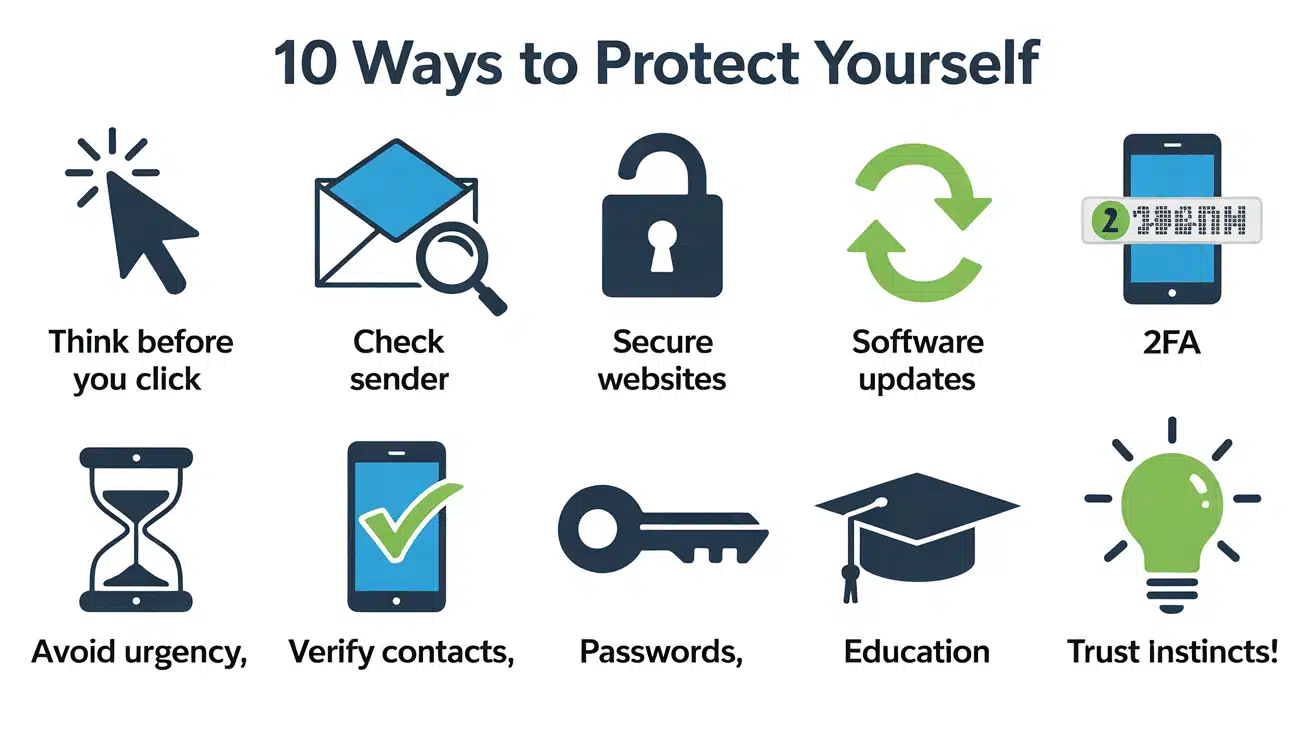
10 Ways to Protect Yourself From Phishing
Here are the most effective steps to keep yourself safe from phishing attacks.
1. Think Before You Click
Never click links in suspicious emails or texts. When in doubt, visit the company’s official website directly. This simple habit can prevent most phishing attacks from succeeding.
Take a moment to pause and question why you received this message. Most legitimate companies will give you time to respond and won’t pressure you with urgent deadlines.
2. Check the Sender Carefully
Look at email addresses closely. Scammers often use addresses that appear similar to genuine ones but have minor differences.
For example, support@amazom.com instead of suport@amazon.com. Pay attention to the domain name after the @ symbol.
Real companies use consistent email formats and refrain from sending messages from free email services like Gmail or Yahoo for official business purposes.
3. Look for HTTPS
Real websites use “https://” (with two slashes), not “https:/”. The “s” means the site is secure. Also, check for a lock icon in your browser address bar.
If you see warnings about unsafe connections or invalid certificates, leave the site immediately. Legitimate financial and shopping websites always use proper security certificates that browsers can verify.
4. Keep Software Updated
Use the latest versions of your browser, email program, and security software. Updates often fix security problems that criminals try to exploit.
Enable automatic updates when possible to stay protected against new threats. Old software versions have known weaknesses that make it easier for phishing attacks to succeed on your device.
5. Use Two-Factor Authentication
Add an extra layer of security to your accounts. Even if criminals get your password, they can’t access your account without the second verification step.
This protection works through text messages, authentication apps, or physical security keys. Enable this feature on all important accounts, such as banking, email, and social media, for maximum protection.
6. Be Suspicious of Urgent Messages
Real companies rarely demand immediate action through email. If a message creates panic or pressure, it’s likely fake and designed to prompt you to act without thinking.
Scammers use fear tactics to bypass your logical thinking and push you into quick decisions. Take time to research and verify any urgent requests before responding or clicking anything.
7. Verify Before You Trust
If you get a suspicious message claiming to be from a company, contact them directly. Use a phone number from their official website, not from the suspicious message.
Ask the company’s customer service if they sent you the message in question. Many companies also have dedicated fraud departments that can quickly confirm whether communications are legitimate or fake.
8. Use Strong, Unique Passwords
Don’t use the same password for multiple accounts. Consider a password manager to help you create and remember strong, unique passwords for every account.
Good passwords include a mix of letters, numbers, and symbols that don’t relate to personal information.
If one account gets compromised, unique passwords prevent criminals from accessing your other accounts.
9. Educate Yourself and Others
Stay informed about new phishing tricks and methods. Share what you learn with family and friends to help protect them, too.
Read security blogs, follow cybersecurity news, and learn about the latest scam techniques. The more people are aware of these threats, the harder it becomes for criminals to find victims.
10. Trust Your Instincts
If something feels wrong, it probably is. It’s better to be cautious and miss a legitimate message than become a victim of fraud.
Your gut feeling often picks up on subtle details that your conscious mind might miss. Don’t ignore that uncomfortable feeling when something seems off about an email, text, or phone call.
Red Flags: How to Spot Phishing Attempts
Learn to recognize these common warning signs that indicate a phishing attempt.
| Red Flag | What to Look For |
|---|---|
| Urgent language | “Act now!” “Limited time!” “Account suspended!” |
| Generic greetings | “Dear valued customer,” instead of your name |
| Suspicious links | Hover over links to see where they really go |
| Poor spelling | Professional companies proofread their messages |
| Unexpected attachments | Don’t open files you weren’t expecting |
| Requests for information | Real companies don’t ask for passwords via email |
What to Do If You Fall for a Phishing Scam?

If you think you’ve been tricked, don’t panic, but act quickly to limit the damage. Don’t pani,c but act quickly:
- Change your passwords immediately
- Contact your bank if financial information was involved
- Run a security scan on your computer
- Monitor your accounts for suspicious activity
- Report the scam to the FBI’s IC3 website
- Learn from the experience to avoid future attempts
Conclusion
Phishing attacks are serious threats, but they’re not impossible to stop. The key is staying alert and knowing what to look for.
Remember that legitimate companies will never ask for sensitive information through email or text messages.
By following the protection tips we covered, you can keep your personal information safe from these scams. Always trust your instincts and take a moment to verify suspicious messages before taking any action.
The best defense against phishing is education and awareness. The more you understand about these tactics, the better you can protect yourself and help others stay safe online, too.
What’s your experience with phishing attempts? Have you spotted any suspicious messages lately? Share your thoughts in the comments below, your story might help others stay safe too!