Have you ever imagined losing all your important files in seconds? Your family photos, work documents, and personal memories could vanish with just one wrong click.
This nightmare becomes reality for millions of people every year through ransomware attacks.
Ransomware is malicious software that locks your files and demands payment for their return. It spreads through email attachments, infected websites, and USB drives.
The good news? You can protect yourself with the right knowledge and tools.
In this blog, I’ll explain what ransomware is, how cybercriminals spread it, and provide practical ways to keep your data safe.
What Is Ransomware?
Ransomware is malicious software that encrypts your files and demands payment for the decryption key. Think of it as a digital kidnapper that holds your data hostage.
Ransomware attacks have increased by 400% in recent years, making it one of the fastest-growing cybersecurity threats.
This type of malware can target anyone, from individuals to large corporations, and result in significant financial losses.
Here’s how it works:
- Malware infects your computer or device – Usually through email or infected websites
- It encrypts (locks) your important files – Makes them completely inaccessible
- A ransom note appears on your screen – Contains payment instructions
- Criminals demand payment in cryptocurrency – Usually Bitcoin for anonymity
- They promise to return your files after payment, but often don’t keep their word
Types of Ransomware
| Type | Description | Impact |
|---|---|---|
| Crypto Ransomware | Encrypts your files but leaves the system functional | Can use a computer but can’t access documents, photos, or videos |
| Locker Ransomware | Completely locks you out of your device | Can’t access anything until the ransom is paid |
| Scareware | Displays fake warnings about infections | Tricks users into downloading more malware or paying for fake security |
How Ransomware Spreads?
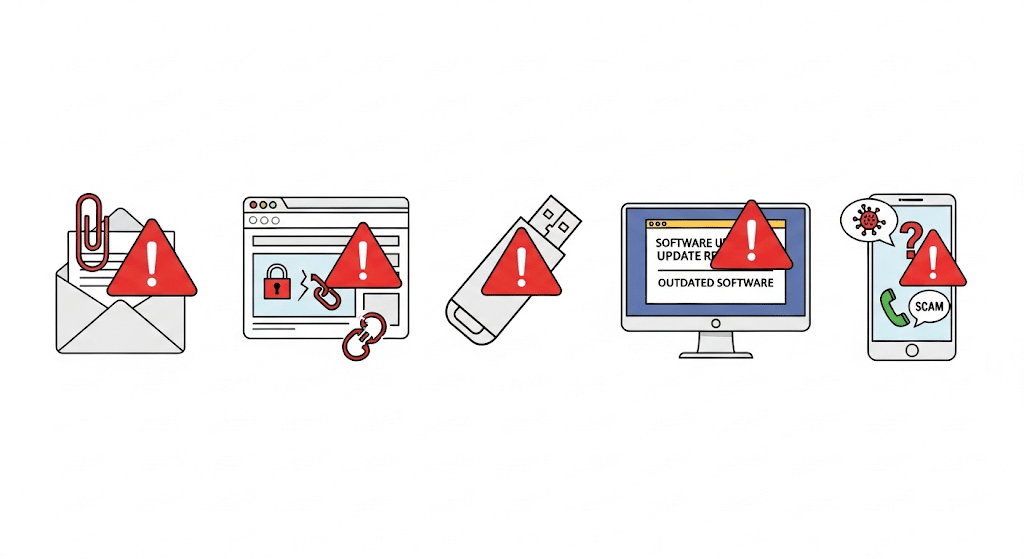
Understanding how ransomware spreads is your first step toward protection. Cybercriminals employ various methods to infect devices and steal sensitive data.
1. Email Attachments
Email remains the most common method by which ransomware enters your system. Criminals send millions of fake emails every day, hoping someone will click.
- Fake invoices or receipts from unknown companies
- Suspicious ZIP files claiming to contain important documents
- Documents that look official but contain hidden malware
- Links to infected websites disguised as legitimate content
2. Infected Websites
Visiting certain websites can automatically download malware to your device. This happens without you clicking anything or giving permission.
- Adult content sites often contain hidden malicious code
- Illegal download sites bundle malware with pirated software
- Compromised legitimate websites are infected by hackers
- Pop-up ads with malicious code that runs automatically
3. USB Drives and External Storage
Physical devices can carry ransomware from one computer to another. Many people are unaware that their USB drives are infected.
- Infected flash drives found in public places
- External hard drives from unknown sources or infected computers
- SD cards from compromised devices or cameras
- Portable storage devices are shared between multiple users
4. Software Vulnerabilities
Outdated software contains security holes that criminals exploit. These weaknesses give them easy access to your system.
- Outdated operating systems are missing critical security updates
- Unpatched security holes in popular programs
- Old versions of web browsers and plugins
- Weak remote access tools with poor security
5. Social Engineering
Criminals trick people into installing malware by pretending to be someone trustworthy. They use psychology to bypass technical security measures.
- Phone calls pretending to be tech support from Microsoft or Apple
- Text messages with malicious links claiming urgent action is needed
- Social media messages from fake accounts of friends or family
- Fake software updates that install malware instead
12 Ways to Protect Your Data from Ransomware
Prevention is your best defense against ransomware attacks. These proven methods will keep your files safe from cybercriminals.
1. Keep Regular Backups
Backups serve as your safety net in the event of a ransomware attack. Store copies of important files in multiple locations to prevent losing all of them.
Regular backups ensure you can restore your data without falling victim to data theft or other cybercrimes.
- Back up files daily to external drives
- Use cloud storage services for automatic backups
- Test your backups monthly to ensure they work
- Store backups offline when not in use
2. Update Your Software Regularly
Software updates fix security holes that criminals exploit. Keeping everything up to date makes it much harder for malware to infect your system. Most successful attacks target outdated software with known vulnerabilities.
- Install security patches immediately when available
- Enable automatic updates for convenience and speed
- Update your antivirus software to catch new threats
- Keep your operating system current with the latest versions
3. Use Strong Antivirus Protection
Quality antivirus software blocks most ransomware before it reaches your files. Modern security programs employ multiple layers of protection to detect threats that other methods may overlook. This creates a strong barrier between you and cybercriminals.
- Install reputable antivirus software from trusted companies
- Enable real-time scanning for constant protection
- Run full system scans weekly to catch hidden threats
- Keep virus definitions updated for the newest protection
4. Be Careful with Email Attachments
Email attachments are the most common method by which ransomware spreads. Always verify who sent the email and why before opening any attachment. When in doubt, contact the sender via an alternative method to confirm.
- Don’t open unexpected attachments from unknown senders
- Verify sender identity before clicking any links
- Scan attachments with an antivirus before opening them
- Delete suspicious emails immediately without reading
5. Avoid Suspicious Websites
Some websites automatically download malware when you visit them. Stick to trusted sites and be extra careful with links from emails or social media. Your browsing habits directly impact your security risk.
- Don’t visit illegal download sites or file-sharing platforms
- Be cautious with pop-up ads that claim urgent action is needed
- Check website URLs carefully for misspellings or odd domains
- Use ad-blocking software to reduce malicious advertisements
6. Enable Firewall Protection
Firewalls monitor network traffic and block suspicious connections. They act like security guards for your internet connection, stopping unauthorized access attempts. This prevents many automated attacks from reaching your computer.
- Turn on your built-in firewall in system settings
- Configure firewall settings to block unnecessary programs
- Monitor incoming and outgoing traffic for unusual activity
- Block unnecessary network access for unused programs
7. Use Strong Passwords
Weak passwords make it easy for criminals to access your accounts and spread malware. Strong, unique passwords for each account make it much harder for hackers to gain access. Password managers help you create and remember complex passwords easily.
- Create unique passwords for each account you use
- Use password managers to generate strong passwords automatically
- Enable two-factor authentication whenever possible for extra security
- Change default passwords immediately on new devices
8. Limit User Privileges
Admin accounts have full system access, which can facilitate the rapid spread of malware if they are infected. Using standard user accounts limits the actions malware can take on your system. This simple change prevents many successful attacks.
- Don’t use admin accounts for daily computer tasks
- Restrict user permissions to only what’s needed
- Control software installation rights carefully
- Monitor user account activities for suspicious behavior
9. Educate Yourself and Others
Knowledge is your most effective defense against cybercriminals. Understanding current scam tactics helps you recognize and avoid threats before they cause damage. Share what you learn with family and coworkers to protect them, too.
- Learn about current scam tactics and warning signs
- Share knowledge with family members and friends
- Train employees in your business about security threats
- Stay informed about new threats through security news
10. Disable Macros in Office Documents
Macros are small programs inside documents that can contain malware. Many ransomware attacks use infected documents with malicious macros. Disabling them by default prevents this common attack method.
- Turn off auto-execution of macros in document settings
- Only enable macros from trusted sources you know
- Use protected view mode for documents from the internet
- Scan macro-enabled files carefully before opening
11. Secure Your Network
Unsecured networks enable criminals to remotely access your devices. Strong network security prevents unauthorized access and stops malware from spreading between devices. This protects all devices connected to your network.
- Use strong WiFi passwords with complex characters
- Hide your network name (SSID) from public view
- Disable WPS (WiFi Protected Setup) for better security
- Monitor connected devices regularly for unknown access
12. Create an Incident Response Plan
Having a plan ready helps you respond quickly if ransomware strikes. Quick action can limit damage and speed up recovery. Practice your response plan so you know exactly what to do under pressure.
- Know what to do if infected with step-by-step instructions
- Have emergency contact numbers ready for help
- Document your recovery steps for future reference
- Practice your response plan with family or team members
What to Do If You’re Infected
Quick action can limit damage if ransomware hits your system. Don’t panic, but move fast to contain the threat.
If ransomware hits your device:
- Disconnect from the internet immediately
- Don’t pay the ransom – there’s no guarantee you’ll get your files back
- Contact law enforcement – report the crime
- Check your backups – restore from clean backups if available
- Seek professional help – consult cybersecurity experts
- Learn from the experience – improve your security measures
Final Thoughts
Ransomware attacks continue to grow, but you don’t have to become a victim. By following these protection methods, you can significantly reduce your risk and keep your data safe.
Remember, prevention is always better than recovery. Regular backups, software updates, and careful online behavior form your first line of defense. The key is building good security habits and sticking to them.
Cybersecurity doesn’t have to be complicated. Small, consistent actions make a big difference in protecting your digital life.
What security measures do you currently use to protect your files? Share your thoughts in the comments below!